Static Inbound and Outbound IPs for n8n Workflows
The complete network layer for n8n.
Shield your webhooks from inbound attacks and route outbound node traffic through a dedicated, verifiable identity.
From basic Static IPs to full HIPAA Shield compliance.
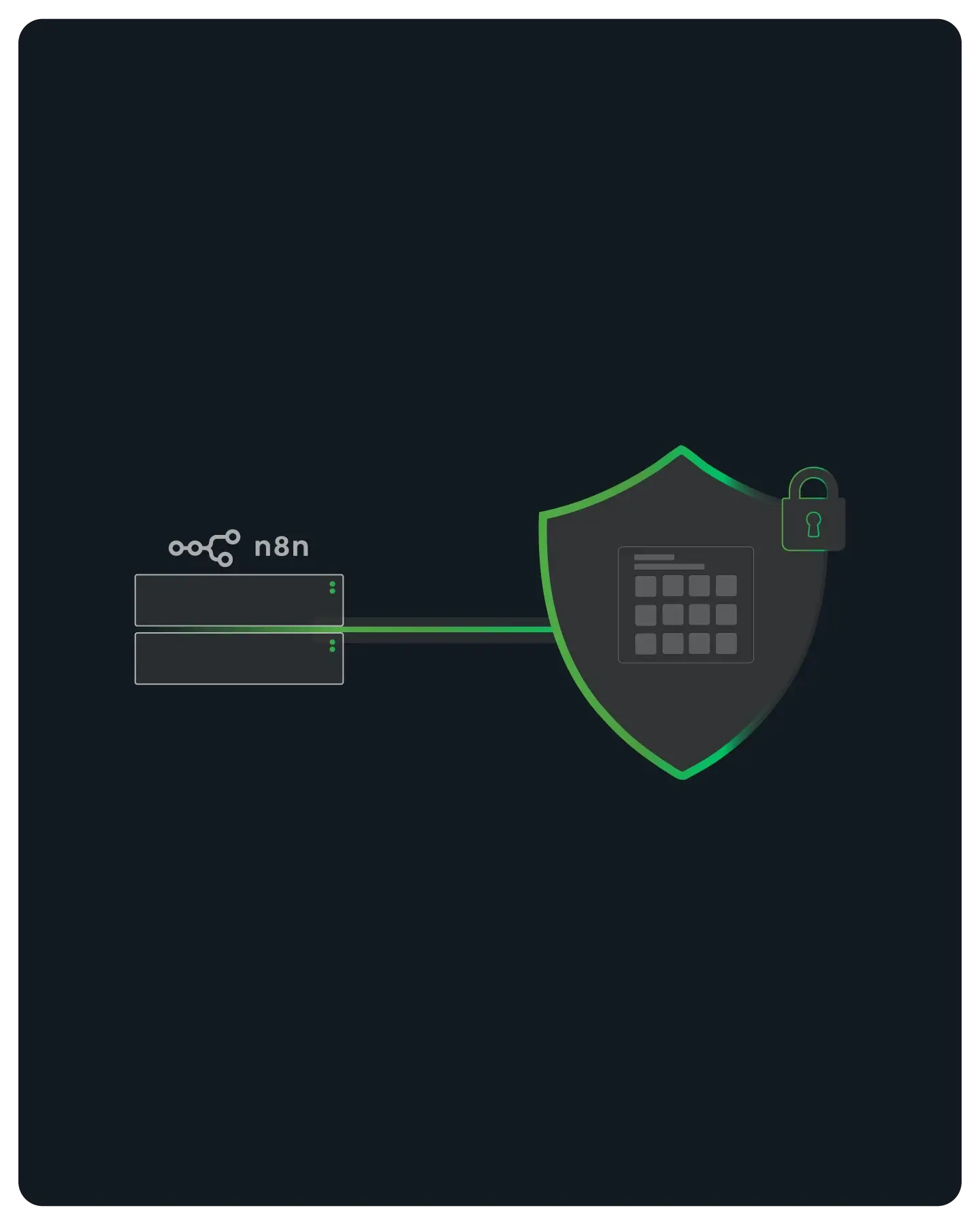
Security & Compliance Without Compromise
Ensure true End-to-End Encryption (E2EE) with SSL Passthrough to protect your most sensitive business data.
We route your traffic without ever holding the decryption keys, making it the only technical path for n8n users in regulated industries to satisfy stringent security audits.
True E2EE (SSL Passthrough)
Unlike standard proxies that decrypt your traffic, QuotaGuard Shield uses SSL Passthrough to maintain a secure tunnel.
The encryption handshake happens strictly between your partner and your n8n server; we route the traffic but never possess the keys to decrypt your payload.
HIPAA & PCI-DSS Compliance
By maintaining strict E2EE, Shield satisfies the technical safeguards required for HIPAA and PCI-DSS compliance.
Because we cannot decrypt the payload, your regulated data remains isolated from third-party exposure during every step of your automation.
No Data Retention or Logging
We operate with a strict No Data Retention policy to minimize your third-party risk profile.
We do not store traffic logs or inspect payloads, ensuring that your sensitive business logic and customer data remain private and off our servers.

Enterprise Control & Scalability
Manage risk and reputation with dedicated infrastructure and region-locked sovereignty for production-grade n8n clusters.
Eliminate the "noisy neighbor" effect and ensure that your automated workflows are compliant with local data residency laws anywhere in the world.
FAQs
Answers to your technical questions about securing n8n egress traffic.
If running n8n via Docker, simply pass the HTTP_PROXY and HTTPS_PROXY environment variables with your QuotaGuard connection string in your docker-compose.yml file.
n8n will automatically route outgoing requests through our static IP.
Yes.
You can configure the proxy settings within the desktop application or run a local tunnel (using qgpass) to route traffic from your local development environment through the static IP for testing.
Yes, for the HTTP Request node. You can manually configure the proxy settings inside the HTTP Request node on the n8n Cloud version.
However, for global environment variable injection, a self-hosted instance provides more control.
Yes.
Standard HTTP proxies cannot handle raw SQL traffic, but QuotaGuard includes a SOCKS5 proxy.
You can use our local tunnel wrapper to route your n8n Postgres node traffic securely into your firewalled database.
No.
QuotaGuard is an infrastructure connectivity tool designed for reliability, not a rotating proxy pool for anonymity.
We do not support web scraping of consumer platforms that block cloud traffic.
Our infrastructure is designed for low latency.
By choosing from one of our 10 global regions (US-East, EU-West, etc.) that matches your n8n hosting location, the latency overhead is negligible (typically <20ms), even for high-volume execution.
If a node fails, you can check the QuotaGuard dashboard for real-time traffic logs.
This will confirm if the request reached our proxy and if it was rejected by the destination server (e.g., a 403 Forbidden vs. a connection timeout).
We highly recommend it, most of our engineering teams practice this security measure to protect their production IP identification to outside parties.
Using separate QuotaGuard subscriptions (or users) for Dev and Prod ensures that testing data never accidentally pollutes your production databases or API logs.
Please Contact Us if you need help with setting up one paying subscription with both production, staging, and development environments.
Still have questions?
We don’t outsource Support to non-Engineers.
Reach out directly to the Engineers who built Shield to discuss your specific architecture, integration challenges, or compliance constraints here 👇
🚀 Ready to Get Started? Choose Your QuotaGuard Path
QuotaGuard STATIC
QuotaGuard SHIELD
Trusted by Engineering Teams Everywhere
Reliability Engineered for the Modern Cloud
For over a decade, QuotaGuard has provided reliable, high-performance static IP and proxy solutions for cloud environments like Heroku, Kubernetes, and AWS.
Get the fixed identity and security your application needs today.

