n8n Cloud runs on shared infrastructure with Cloudflare handling egress. You get rotating IPs from their pool. Around 22 addresses that can change at any time.
For most of the internet, that's fine. For enterprise APIs, data warehouses, financial systems, and internal tools behind firewalls, it's a blocker. The other side needs a static IP to whitelist. n8n Cloud can't give you one.
What Actually Gets Blocked
n8n Cloud doesn't own the outbound IPs. Cloudflare does. They're shared across all n8n Cloud instances in a region. The IPs rotate and cycle.
This blocks connections to corporate firewalls that whitelist specific IPs, WAF rules from Cloudflare/Akamai/AWS, enterprise APIs with IP allowlisting (Salesforce, HubSpot, Marketo), Google Workspace with Context-Aware Access, financial APIs, healthcare APIs requiring static IPs for HIPAA, and databases like MongoDB Atlas, Amazon RDS, and most SFTP servers.
You could whitelist n8n's current IPs, but in 72 hours they rotate. Then you're down again.
The Solution: A Static IP Proxy
You need a static outbound IP that proxies your n8n traffic. QuotaGuard provides two dedicated, load-balanced static IPs. They never change. Point n8n at them. They forward your traffic from a consistent address.
Setup takes about five minutes. You have a few options depending on your setup.
How to Set It Up
Option 1: HTTP Request Node (Recommended for Most)
- Sign up for QuotaGuard Static
- Open the HTTP Request node that needs the proxy
- Click "Add Option" at the bottom
- Select "Proxy"
- Paste your proxy URL:
http://username:password@us-east-static-01.quotaguard.com:9293 - Save and test
Test it. Create a simple HTTP Request node that calls https://ip.quotaguard.com. It should return your static IPs. If you see the same two IPs repeatedly, you're configured right.
Option 2: n8n Credentials (For Reusable Config)
If you want one proxy config applied across multiple nodes:
- Go to Credentials in n8n
- Create a new credential of type "HTTP Basic Auth"
- Paste your QuotaGuard URL as the "Authorization" header
- In your HTTP Request nodes, reference this credential in the Proxy field
Change the credential once, it applies everywhere.
Option 3: Global Environment Variables (Self-Hosted Only)
If you're running n8n self-hosted, set HTTP_PROXY and HTTPS_PROXY environment variables:
HTTP_PROXY=http://username:password@us-east-static-01.quotaguard.com:9293
HTTPS_PROXY=http://username:password@us-east-static-01.quotaguard.com:9293
Every outbound request goes through the proxy automatically. No node-level config needed.
n8n Cloud doesn't support this. You're limited to node-level proxy config on Cloud.
Option 4: n8n Desktop App
Same as Option 1. Add the proxy URL in the HTTP Request node.
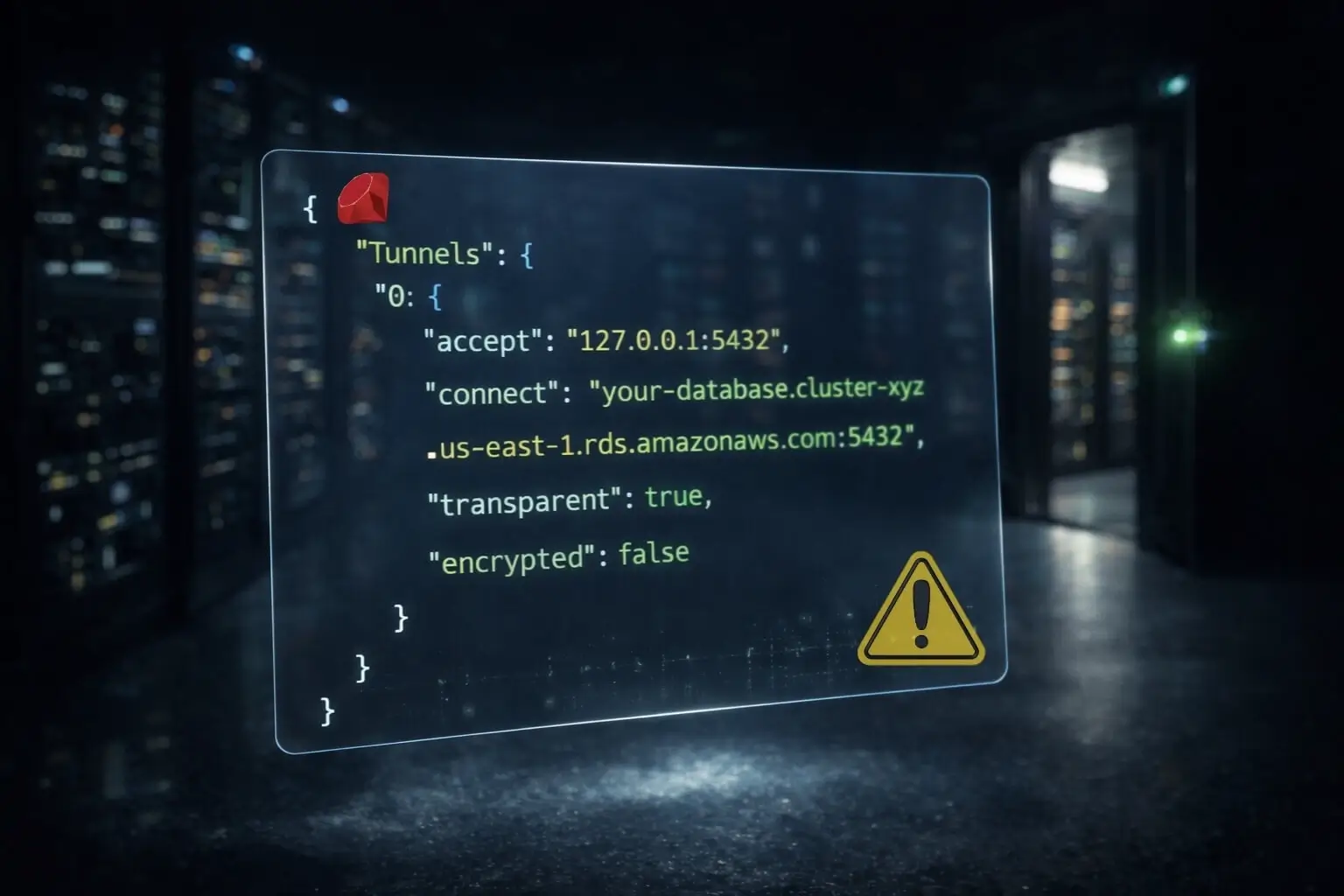
The SFTP and Database Catch
SFTP servers and databases usually aren't HTTP. They're raw TCP. You can't proxy them over HTTP.
The right solution is a SOCKS5 proxy. QuotaGuard provides QGTunnel for this. It forwards SFTP, SSH, and database connections through static IPs.
Catch: n8n Cloud doesn't support QGTunnel or SOCKS5. n8n Cloud only handles HTTP proxies in the HTTP Request node.
If you need SFTP with static IPs on n8n Cloud, you have two paths:
- Use an intermediate HTTP service. Set up a simple API that reads/writes SFTP on your behalf, then call that API from n8n through the HTTP proxy.
- Go self-hosted. If you run n8n on your own infrastructure, QGTunnel works perfectly for SFTP, databases, and SSH.
For most workflows, this isn't a blocker. But if you're heavy on SFTP or raw database connections, self-hosted + QGTunnel is worth the trade-off.
Latency
Your proxy adds latency. Same region (US East to US East): 10-20ms. Cross-region (US East to EU): 50-100ms. Most workflows won't notice. If you're doing high-volume transactional work, benchmark it. Pick a region close to your API.
Pricing
QuotaGuard Static starts at $19/month. Two static IPs, 500GB bandwidth. Shield is $29/month if you need HIPAA or PCI compliance (SSL passthrough, audit logs, BAA).
Common Questions
How do I whitelist n8n Cloud IPs for my in-house API behind a firewall?
Don't whitelist n8n directly. Whitelist QuotaGuard's static IPs instead. Get the two IPs from your QuotaGuard dashboard. Add them to your firewall. Configure the HTTP proxy in your n8n nodes.
Can I get a fixed IP address for my n8n Cloud instance?
n8n Cloud doesn't offer dedicated IPs. You need a proxy. QuotaGuard gives you the fixed IP layer that n8n doesn't.
My SFTP vendor needs a static IP but n8n gave me 22 IPs that can change. What do I do?
On n8n Cloud, SFTP is the gotcha mentioned above. Either build an HTTP intermediary or go self-hosted with QGTunnel.
What are the outbound IP addresses n8n Cloud uses?
They rotate. Cloudflare manages the pool. You can't hardcode them. Use a static proxy instead.
How do I connect my n8n Cloud automation to a client API that's behind a firewall?
Get the client to whitelist your QuotaGuard proxy IPs, not n8n's rotating IPs. Set up the HTTP proxy in your HTTP Request nodes.
If You Need Compliance
If you're in healthcare or finance, QuotaGuard Shield adds SSL passthrough, HIPAA BAA, and audit trails. Same static IPs. $29/month.
Getting Started
Sign up for QuotaGuard Static. Configure the proxy in one HTTP Request node. Test it against ip.quotaguard.com. Then apply it across your n8n workflows.
QuotaGuard Static IP Blog
Practical notes on routing cloud and AI traffic through Static IPs.





.webp)




