You deploy your app to Render, connect to MongoDB Atlas, and hit this error:
MongooseServerSelectionError: Could not connect to any servers in your MongoDB Atlas cluster.
One common reason is that you're trying to access the database from an IP that isn't whitelisted.Or you try to call a partner API and get a 403 Forbidden. The payment gateway rejects your requests. The corporate firewall blocks your webhook.
The problem is the same every time: Render's dynamic infrastructure means your app's outbound IP can change during deploys, scaling events, or infrastructure updates. The service you're trying to reach doesn't recognize you.
This guide covers your options for getting static outbound IPs on Render, from native features to third-party proxies, with working code examples.
Quick Comparison
Before diving into details, here's a quick comparison of your options:
| Feature | Render Native (CIDR Ranges) | QuotaGuard Static |
|---|---|---|
| IP Type | Shared CIDR range (e.g., /24 = 256 IPs) | 2 dedicated static IPs |
| Setup | None (built-in) | Environment variable |
| Database Connections (SOCKS5) | ❌ No | ✅ Yes |
| Exclusive to Your App | ❌ No (shared regionally) | ✅ Yes |
| Pre-2022 Oregon Workspaces | ❌ Not supported | ✅ Works |
| Cost | Free | Starts at $19/month |
| Best For | APIs that accept CIDR ranges | Strict firewalls, databases, compliance |
Option 1: Render's Native Outbound IPs
Render provides shared outbound IP ranges for every service. For many use cases, these are sufficient.
How to Find Your Outbound IPs
- Open the Render Dashboard
- Click your service to open its details page
- Click the Connect dropdown in the upper right
- Switch to the Outbound tab
- Copy the listed IP ranges
Important Caveats
IPs are CIDR ranges, not individual addresses. A /24 range means 256 possible IPs. Virginia (US-East) has the broadest ranges. Other regions have smaller pools.
IPs are shared across all Render customers in your region. If another customer abuses the IP and gets it blocked, your app could be affected too.
Pre-January 2022 Oregon workspaces have no static outbound IPs. If your workspace predates this, the Outbound tab won't appear. You'll need a proxy service.
IP ranges changed in November 2025. Render migrated to new outbound IP ranges. If you previously allowlisted their old individual IPs, those no longer work.
When Native IPs Work Fine
- Target service accepts CIDR range notation
- You don't mind sharing IPs with other Render customers
- HTTP/HTTPS requests only (no database tunneling)
- IP reputation isn't critical for your use case
When Native IPs Fall Short
- Target only accepts individual IPs (many corporate firewalls, legacy systems)
- You need SOCKS5 for database connections (MongoDB, PostgreSQL, MySQL)
- Compliance requires documented, exclusive IP provenance
- You're on an old Oregon workspace with no native static IPs
- Concerned about "noisy neighbor" IP reputation issues
Option 2: QuotaGuard for Dedicated Static IPs
When Render's native CIDR ranges aren't enough, a proxy service gives you dedicated static IPs that only your app uses.
QuotaGuard provides two load-balanced static IPs exclusive to your account. It works with any Render service type: Web Services, Background Workers, and Cron Jobs.
Setup Steps
- Sign up at quotaguard.com/products/pricing
- Copy your
QUOTAGUARDSTATIC_URLfrom the dashboard - In Render, go to your service → Environment → Add Environment Variable
- Add
QUOTAGUARDSTATIC_URLwith your proxy URL - Update your application code to route requests through the proxy
Node.js Example
Using https-proxy-agent:
const HttpsProxyAgent = require('https-proxy-agent');
const agent = new HttpsProxyAgent(process.env.QUOTAGUARDSTATIC_URL);
const response = await fetch('https://api.example.com/data', {
agent: agent
});Python Example
Using requests:
import os
import requests
proxies = {
'http': os.environ.get('QUOTAGUARDSTATIC_URL'),
'https': os.environ.get('QUOTAGUARDSTATIC_URL')
}
response = requests.get('https://api.example.com/data', proxies=proxies)Go Example
package main
import (
"net/http"
"net/url"
"os"
)
func main() {
proxyURL, _ := url.Parse(os.Getenv("QUOTAGUARDSTATIC_URL"))
client := &http.Client{
Transport: &http.Transport{
Proxy: http.ProxyURL(proxyURL),
},
}
resp, err := client.Get("https://api.example.com/data")
}Ruby Example
require 'uri'
require 'net/http'
proxy = URI(ENV['QUOTAGUARDSTATIC_URL'])
uri = URI('https://api.example.com/data')
Net::HTTP.start(uri.host, uri.port,
proxy.host, proxy.port, proxy.user, proxy.password,
use_ssl: uri.scheme == 'https') do |http|
request = Net::HTTP::Get.new(uri)
response = http.request(request)
endDatabase Connections with SOCKS5
HTTP proxies only work for HTTP traffic. Database connections (MongoDB, PostgreSQL, MySQL) use TCP protocols that require SOCKS5 tunneling.
QuotaGuard's QGTunnel handles this by wrapping your application process and routing specified traffic through the SOCKS5 proxy.
Setup Steps
1. Download QGTunnel into your app:
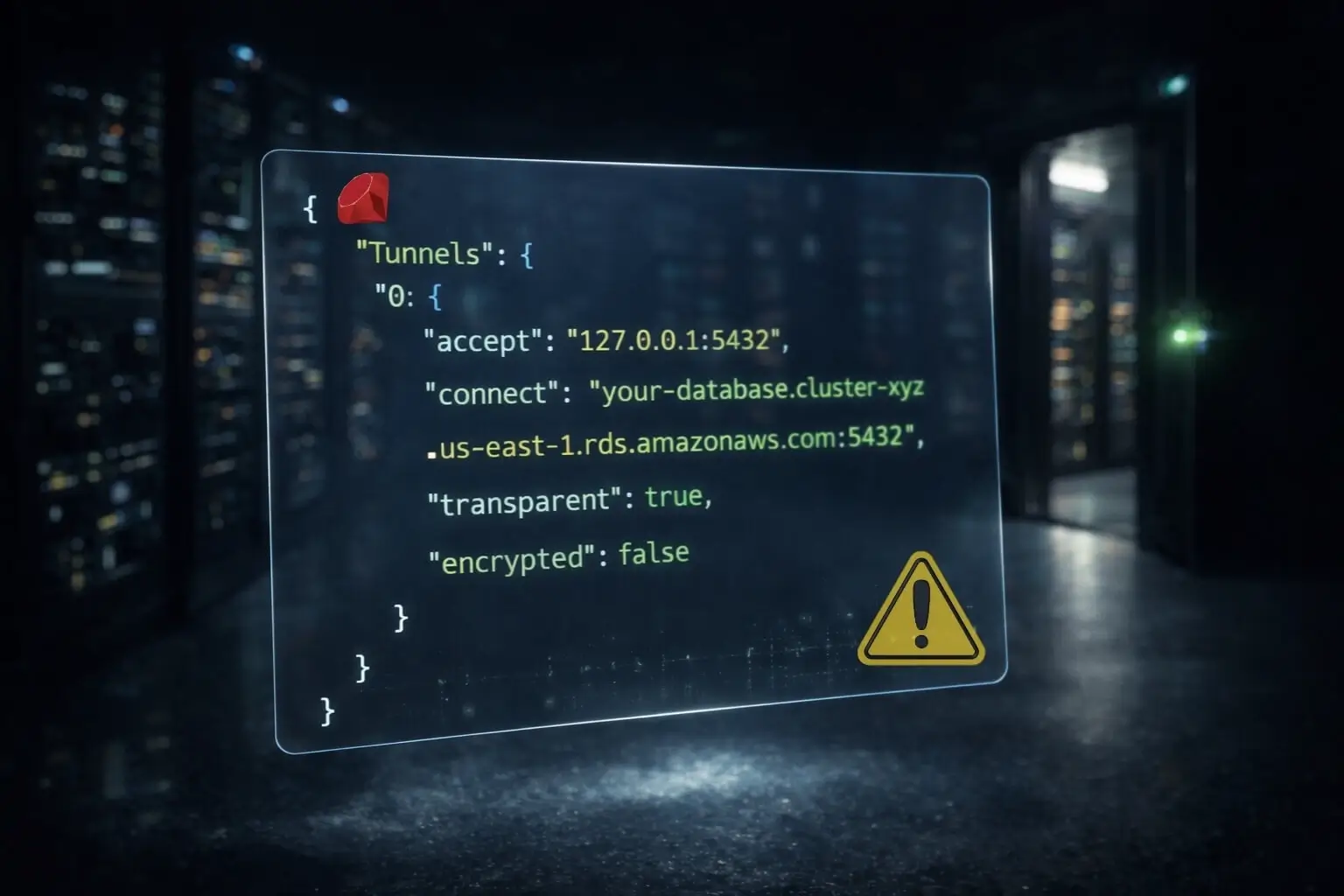
curl https://s3.amazonaws.com/quotaguard/qgtunnel-latest.tar.gz | tar xz2. Configure the tunnel in QuotaGuard dashboard:
Go to Settings → Tunnel → Create Tunnel. For MongoDB:
- Remote Host: your MongoDB Atlas hostname
- Local Port: 27017
- Transparent: true
- Encrypted: false
3. Update your start command:
# Instead of:
npm start
# Use:
./bin/qgtunnel npm startMongoDB Atlas Configuration
- Get your QuotaGuard static IPs from the dashboard
- In MongoDB Atlas, go to Network Access → Add IP Address
- Add both QuotaGuard IPs (you only need to do this once)
- Your Render app now connects through the static IPs
The same QGTunnel approach works for PostgreSQL (port 5432), MySQL (port 3306), and any other TCP-based database.
Verifying Your Static IP
QuotaGuard provides an endpoint that returns your outbound IP. Use it to confirm the proxy is working.
Command line test:
curl -x $QUOTAGUARDSTATIC_URL https://ip.quotaguard.comIn your application (Node.js):
const HttpsProxyAgent = require('https-proxy-agent');
const agent = new HttpsProxyAgent(process.env.QUOTAGUARDSTATIC_URL);
const response = await fetch('https://ip.quotaguard.com', { agent });
const data = await response.json();
console.log('Outbound IP:', data.ip);
// Should return one of your QuotaGuard static IPsWhich Option Should You Choose?
Use Render's native CIDR ranges if:
- Your target service accepts IP ranges (not just individual IPs)
- You're making HTTP/HTTPS requests only
- IP reputation isn't critical for your use case
- Your workspace was created after January 2022
Use QuotaGuard if:
- Target requires individual static IPs (many corporate firewalls, legacy systems)
- You need database connections via SOCKS5 (MongoDB Atlas, PostgreSQL, MySQL)
- You're on a pre-2022 Oregon workspace with no native static IPs
- You need compliance documentation for IP provenance
- You want to avoid shared IP reputation risks
A Note on Render's Roadmap
Render has announced plans for exclusive (non-shared) static IPs, targeted for Q1 2026. When that launches, it may cover some use cases currently requiring a proxy service. However, features like SOCKS5 database tunneling, regional data residency (EU/US), and end-to-end encryption (QuotaGuard Shield) will likely remain differentiators for teams with compliance or infrastructure requirements beyond basic IP allowlisting.
Get Started
QuotaGuard offers a free trial with no credit card required. Setup takes about 5 minutes.
- Render Integration Page – Features and FAQs
- Pricing – Plans starting at $19/month
- Documentation – Language-specific setup guides
Questions? Our support team is engineers, not outsourced help desk. Reach out directly.






.webp)








.webp)




